Secure use of the cloud: When can confidential data be transferred to external cloud services?
ETH Zurich’s new guidelines on the use of cloud services are to be implemented by March 2023. Read on to find out what is changing and what this might mean for your data.

A virtual, integrated working environment is essential in research, teaching and administration at ETH. Cloud services seem to offer a very accessible solution for this.
However, if those cloud services are offered by third-party providers (external IT services), then there is no way of knowing for sure in which country the ETH data will be located, which laws will apply (e.g. with regard to data protection) and how well the provider will protect the data.
For this reason, data classified as “internal” or as “confidential” must never automatically be uploaded into external cloud services – and data classified as “strictly confidential” must never be stored or processed in the cloud at all (cf. Article 22 or Article 22bis of the directive Information Security at ETH Zurich).
Below you will find answers to some of the most frequently asked questions about cloud usage.
Am I generally allowed to use cloud services at ETH for internal and confidential data?
Yes, but only under certain conditions. ETH itself provides its own cloud services. These can of course be used without hesitation, including for data classified as “internal” or “confidential”.
The following in-house cloud services are available:
- polybox: Storage space available to all ETH members. polybox also enables collaborative work on documents. Confidential data may be stored in polybox.
- If a particularly high level of protection for research data is required, the Scientific IT Services offer suitable platforms, such as Leonhard Med.
How can I use external cloud services at ETH?
In this case, criteria are provided that must be used to assess whether an external cloud service is secure enough for “internal” or “confidential” data.
To standardise the use of external cloud services at ETH and in an attempt to ensure sufficient protection of the data to be outsourced, two roles have been defined: service mediators and information owners.
Service mediators
Role: “Service mediators” procure external IT services such as cloud services and are essentially responsible for contract management with the cloud provider. Typically, service mediators are the central IT Services and the IT support groups, but they can also be professors who want to provide a specific cloud service for the members of their group or for their wider institute, department heads or coordinators, administrative department or staff unit heads, etc.
Tasks: In the course of contract management for the external cloud service, the service mediator verifies the level of protection the service offers for the ETH data to be outsourced. Based on this review, the service mediator approves the external cloud service for its intended use by ETH members.
Whether data classified as “internal” or “confidential” may be outsourced to an external cloud service depends on the level of protection this data requires. Examples of criteria to be reviewed include: multi-factor authentication, data protection requirements, server location (should be in Switzerland or the EU), jurisdiction, etc. The complete list can be found in the IT Guidelines and IT Baseline Protection Rules of ETH Zurich (cf. Articles 6, 10 and 11).
Please also note: Data classified as “strictly confidential” must never be outsourced to external cloud services. This means service mediators are not permitted to provide external cloud services for outsourcing “strictly confidential” data.
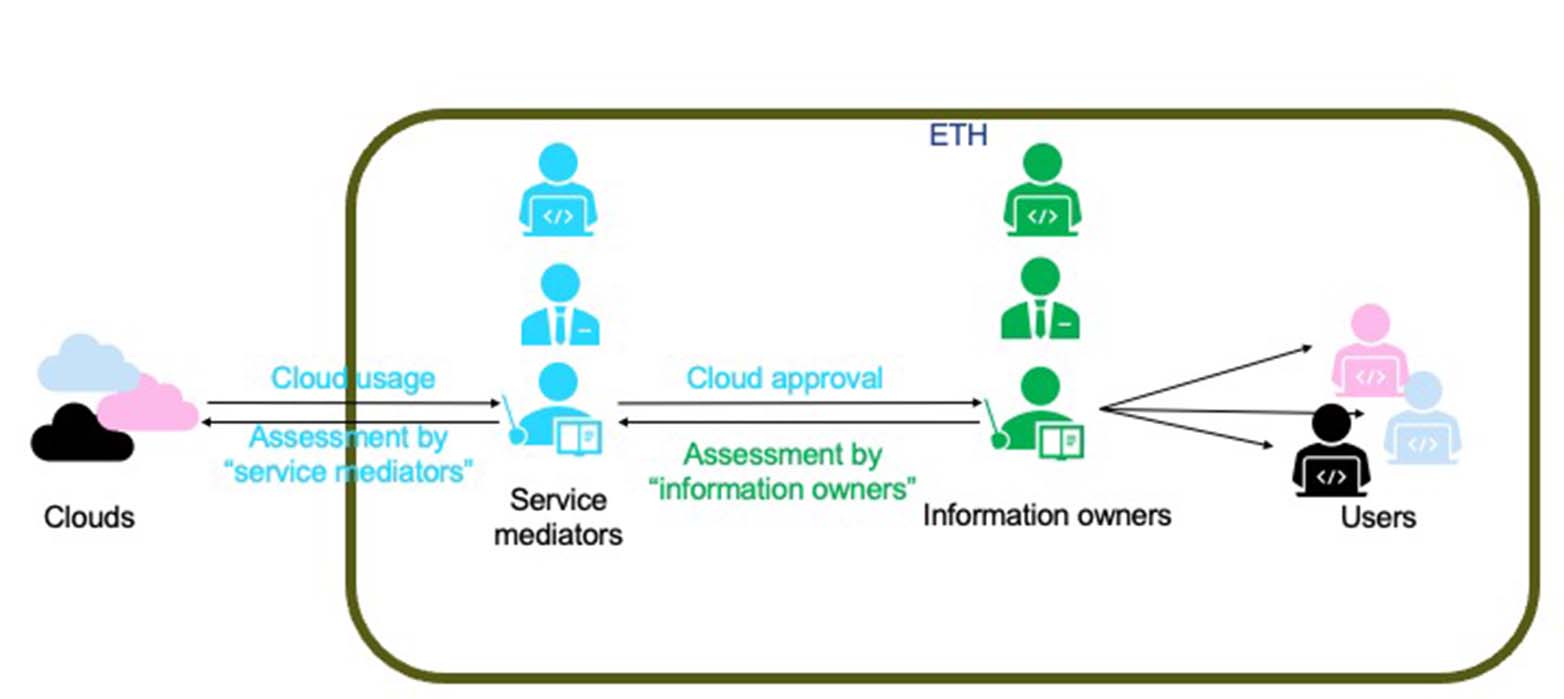
Information owners
Role: The second important role is that of “information owners”. They are responsible for the data that is collected and processed on their behalf and essentially decide whether or not to outsource their data to external cloud services. (Please note: The decision to outsource ETH Zurich data is not the responsibility of the service mediators. The mediators simply arrange an external cloud service and approve that cloud service for a specific use.)
Tasks: Information owners must above all be able to assess whether a cloud service approved for use within ETH meets the protection requirements of their data. It is up to them to assess the risk they are taking by outsourcing their data to the designated cloud service. Depending on the data to be outsourced, this assessment will also determine whether their data may be subject to export controls or whether a data protection impact assessment will be necessary before the data is outsourced to the external cloud service.
It is possible for one person to perform both roles – that of service mediator and that of information owner. For instance, a professor may want to obtain an external cloud service for her own research as well as for the employees of her institute. He/she must then review the criteria according to both of her roles.
Support through questionnaire
For both roles, appropriate questionnaires or assessments will be made available in good time before the directives come into force; service mediators and information owners will fill out the questionnaires and document the assessments in order to be allowed to use their data securely in cloud services. These assessments will be collected with the help of central IT Services (ITS) on behalf of the Chief Information Security Officer (CISO) at ETH with a view to offering a list of verified cloud services and other third-party IT services used at ETH in the future.
Transitional provisions: What changes when?
The regulations on cloud usage as set out in the IT Guidelines and IT Baseline Protection Rules of ETH Zurich are to be implemented by March 2023 (Article 16).
For this reason, it makes sense for service mediators to start reviewing the external cloud services they provide now to determine whether and to what extent they meet the requirements of the IT Guidelines and IT Baseline Protection Rules of ETH Zurich.
Meanwhile, if an information owner wishes to outsource confidential data to an existing external cloud service, they must contact the service provider to clarify whether this is possible and whether the external cloud service already meets the requirements of the IT Guidelines and IT Baseline Protection Rules of ETH Zurich. Outsourcing is then possible only once the information owner has carried out the above-mentioned assessment.
For new external cloud services, the regulations in the IT Guidelines and IT Baseline Protection Rules of ETH Zurich apply with immediate effect.
Assessment forms will soon be made available to assist the service mediator or information owner in their duties.
Domenico Salvati (CISO) about the new guidelines
Domenico Salvati, why were new rules created for cloud usage?
Until now, the use of internal, but especially confidential data in external cloud services has been either not regulated at all or regulated too restrictively. To create a legal basis for this topic, the relevant protection standards have been defined.
If I want to collaborate with an external research partner, I need to use a specific external cloud service. What factors do I have to consider?
If it’s an external cloud service that hasn’t yet been approved for use within ETH, it will first be necessary to set up contract management with the external cloud provider. This puts you in the role of a service mediator, who reviews the relevant external cloud service to see what kind of data the service is suitable for in principle. Only after a positive assessment, for which appropriate documentation will be made available in the coming months, can the external cloud service be approved for use within ETH.
What criteria must be observed if confidential data is to be outsourced to an external cloud service that has already been approved for use within ETH?
In this case, the information owner is responsible for determining the level of protection that the data requires. If the data is classified as “internal” or as “confidential”, it is important to choose a cloud service that has been rated as good for working with this type of data classification. The classification of data as e.g. “internal” or “confidential” is risk-based and is defined in the directive Information Security at ETH Zurich. The appendices to the directive are particularly important here, as they show specific examples of common types of data and the necessary protective measures. Please note: “Strictly confidential” data must never be outsourced to an external cloud service.
Where can I get help evaluating a cloud service as a service mediator?
IT Services can assist you, as can I, with your evaluation.
Where can I find out which cloud services have already been approved for use at ETH?
The approval of external cloud services for ETH data classified as “confidential” has the great advantage that ITS can then add those services to lists on behalf of the CISO. This makes it easy to check whether a desired service has already been checked for suitability and is used elsewhere at ETH.
It can also be helpful to ask in advance whether ETH’s own solutions – such as polybox or the Leonhard Med platform – might also be suitable, as these are much faster and more readily available.

Dr. Domenico Salvati is the Chief Information Security Officer (CISO) at ETH Zurich.
